What Is Zero-Day Vulnerability and How to Protect Against It
Cybersecurity is a constant battle, and one of the most insidious threats is the zero-day vulnerability. These vulnerabilities are exploited by attackers before software developers have a chance to patch them, making them particularly dangerous for websites, applications, and servers.
In this guide, we’ll explain what zero-day vulnerabilities are, why they’re so risky, and how to protect your website effectively—with the help of JumboNIC’s security-focused hosting infrastructure.
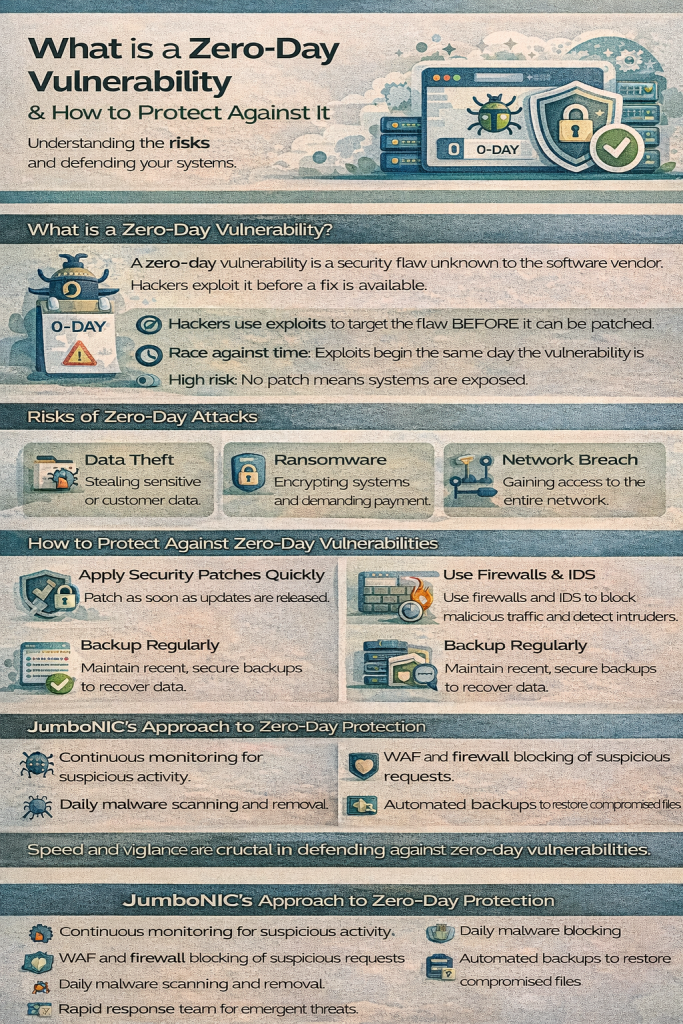
What Is a Zero-Day Vulnerability?
A zero-day vulnerability is a software flaw or security gap that is unknown to the software vendor or developer. The term “zero-day” comes from the fact that the vendor has had zero days to fix it.
Attackers who discover these vulnerabilities can exploit them to:
Gain unauthorized access
Install malware
Steal sensitive data
Disrupt services
Since no patch exists at the time of discovery, zero-day attacks are difficult to defend against and can be devastating if not mitigated quickly.
Why Zero-Day Vulnerabilities Are Dangerous
No Immediate Fix Available
Since the vulnerability is unknown to developers, there’s no patch to prevent attacks.High Risk for All Websites
Small blogs, e-commerce platforms, and enterprise applications alike are vulnerable.Hard to Detect
Zero-day exploits often leave minimal traces, making them challenging to identify before damage occurs.Targeted Attacks
Attackers can use zero-day vulnerabilities for highly targeted attacks, such as stealing credentials or injecting ransomware.
Common Zero-Day Attack Vectors
Web Applications: CMS platforms like WordPress or custom apps with unpatched components.
Operating Systems: Exploiting flaws in Windows, Linux, or macOS.
Browser and Plugins: Vulnerabilities in browsers or extensions can give attackers access to sensitive data.
IoT Devices: Smart devices with unpatched firmware can be exploited.
How to Protect Against Zero-Day Vulnerabilities
While zero-day attacks are inherently difficult to prevent, proactive measures can minimize risk:
1. Keep Software Up-to-Date
Regularly update CMS platforms, plugins, themes, and server software.
Apply patches immediately when available.
JumboNIC Advantage: JumboNIC ensures your hosting environment is always running the latest stable server software and offers automated patching for supported applications.
2. Use a Web Application Firewall (WAF)
A WAF can detect and block suspicious traffic patterns, even if a zero-day vulnerability is being targeted.
JumboNIC Advantage: JumboNIC includes real-time WAF protection, blocking malicious requests before they reach your site.
3. Implement DDoS Protection
Some zero-day exploits are combined with DDoS attacks to overwhelm servers. Protecting your website from volumetric attacks reduces exposure.
JumboNIC Advantage: JumboNIC’s global CDN and DDoS mitigation absorb traffic spikes, keeping your site online.
4. Restrict User Privileges
Limit administrative access to only trusted personnel and use least privilege principles.
Admin accounts: Only essential users
Database access: Limit write permissions
File permissions: Lock down critical directories
5. Enable Strong Authentication
Even if attackers exploit a zero-day, accounts with strong passwords and two-factor authentication (2FA) are harder to compromise.
JumboNIC Advantage: JumboNIC supports 2FA and secure authentication, adding another layer of protection.
6. Monitor and Back Up Regularly
Real-time monitoring detects unusual activity quickly.
Frequent backups ensure you can restore your site in case of a compromise.
JumboNIC Advantage: JumboNIC provides automated daily backups and advanced monitoring, minimizing downtime and data loss.
7. Use Sandboxing and Isolation
Isolate critical applications and services so that a vulnerability in one component does not compromise the entire system.
JumboNIC Advantage: JumboNIC’s hosting infrastructure leverages containerization and secure environments to isolate resources.
Why JumboNIC Is Ideal for Zero-Day Protection
JumboNIC’s platform is built with security-first performance in mind, combining:
Automatic software updates
Real-time firewall and DDoS protection
Global CDN for secure and fast content delivery
Automated backups and monitoring
Support for 2FA and secure authentication
This combination makes it much harder for attackers to exploit zero-day vulnerabilities successfully.
Conclusion
Zero-day vulnerabilities are a serious and unpredictable threat. Since there’s no immediate fix when they are discovered, proactive measures are essential to protect your website and users.
By keeping software updated, implementing strong authentication, using a WAF, and leveraging a security-focused hosting provider like JumboNIC, you can reduce risk, respond faster to threats, and maintain a secure, reliable online presence.

